
As for all initiatives it is always a good idea to create a notion of where we are today and define the “as-is” situation. This makes it easier to define a “desired state” and start looking into steps to get there. We like to look upon digital transformation or innovation as a transition from one state to another desired state. This is why an analysis of the “as is” situation is a good start when kicking off your IAM initiative.
When doing this initial analysis, one thing that you are likely to discover is that your IAM solution is at the heart of your business and therefore critical to the success of any digitally fueled transformation project. IAM has evolved from being a side component in your digital solution to being one of the center pieces to enable digital innovation with remained control and security, while still catering for ease of use and enablement.
Ask yourself; - What would happen to your business if the IAM solution is shut down and no one is granted access? Or; - What would happen if your IAM solution is compromised and the wrong person or system is allowed access to systems and data? The latter may result in a serious security issue, stop in production and a lot of bad will for your brand.
These are a some of the signs that indicates that you need to give your IAM strategy a serious look:
- ”We have multiple identity providers (IdP’s), and multiple realms (security domains), separated from each other, but we really want a single sign on (SSO), for our staff to save time and effort”
- External parties (like customers, citizens or suppliers), also need access to your systems or data – “Do we really want to add externals to our user database (IdP)? Or do we want to leave the identification and trust to someone else (like the IAM system of your customer, Apple, Google or even Facebook)?
- “Our integration and collaboration between systems and data storage are becoming a complex grid of accesses and rights. How can we really maintain a secure network without adding more and more IT-staff to manage the mess?”
- “We frequently discover that accesses and rights still remain even after someone left our company and we don’t really know if our access policy cover when someone leaves, changes department or roles in our organisation.” Is there a common place where you can get an overview, handle changes and add/remove accesses when needed (what is your identity life cycle)?
A complex mix of requirements to manage and prioritize
As users, consumers or partners, we are looking for an “easy flow” through our digital assets – we want a simple enough login for both staff and customers and we want our systems to communicate efficiently using certificates and time limited tokens. Still we claim “Zero trust” and push the usage of regularly changed complex passwords, a second trust source like two/multi factor authentication and other “trust improving actions”.
We want to make sure that external parties don't get access to our secret data or critical systems, and still we want to login “once in the morning and never ever enter a password again”. We make our pass codes and secrets more complex and then we add a password-wallet to store the complex passwords so that we can forget them. The ease of use, user experience and simplicity is a tricky paradox in relation to the necessary security aspects of your IAM strategy and protection of digital assets.
Simply put; It’s a complex mix of requirements to manage and prioritize between.
The first step of your journey towards a well functioning IAM strategy and capability, is to figure out how mature your IAM policy and tooling is today. Secondly you need to define a desired state and where you want it to be tomorrow. When that is done, it is time to start moving and get your initiative and policy going. More on this in coming blog posts…
To assist with your maturity analysis and define what your “as-is” situation is, we have created the below steps. These shows a common maturity process for organisations IAM journeys today and most organisations of today can find their current state in any of these stages.
The IAM maturity process
The picture below show some typical stages in the IAM maturity process.
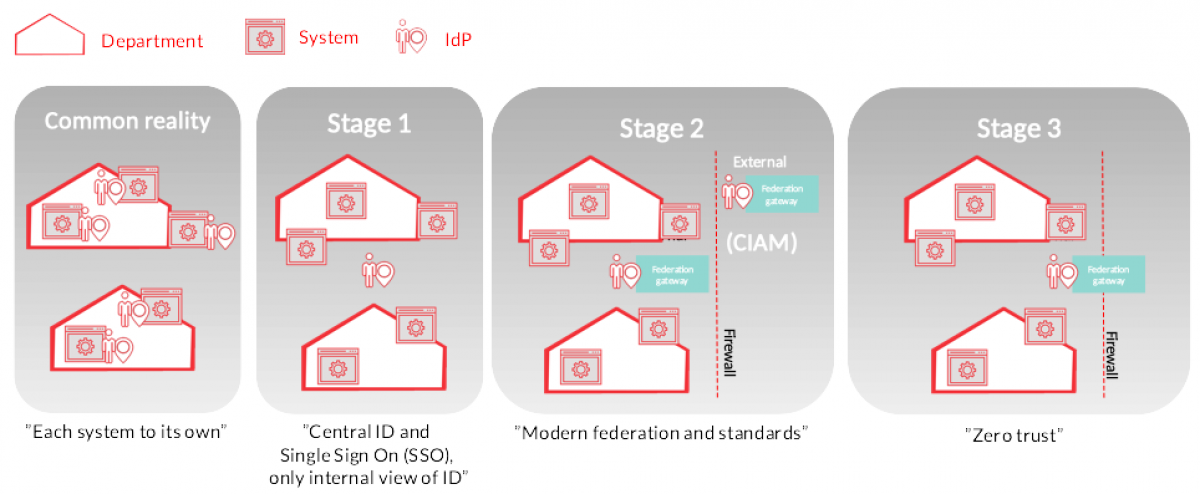
The 4 steps of IAM maturity
- Step 1 – Common reality: This is the first step in the IAM maturity process. In these step each system, run by separate departments, have their own identity provider/user store. This means that users/systems are able to access the system if they exist in the local user database and has the right credentials. As there is no integration/access between different user stores, every user has to be created for each system with their own password and login credentials.
- Step 2 – SSO: In this step, the organization has implemented a centralized identity provider. This means that as long as the various systems have integrated with this, users only need to exist in one user store and that credentials for various systems are attached to this user. For users this is a significant improvement from step 1, as it makes it possible for them to authenticate with one user id and password for different systems. It also makes it easier for the organization to administer users and credentials across the organization in one place. This is probably also a common IAM maturity level for many organizations.
- Step 3 – Modern federation and standards: When reaching this step, the organization has realized that not all users that one has to manage are internal or can be managed through one single IdP instance. A modern organization also has to manage the authentication and authorization of external partners, customers, citizens or other stakeholders. This is often done by federation of the identity and authentication process. This is accieved by deciding to trust selected external IdP’s or user stores. Basically this means that if the user is authenticated by an external trusted source, we also trust that this user or system is who he/she claims to be and granted access in accordance with previously agreed policy. Trusted external sources can for instance be general trusted user stores (like BankID for Sweden), governmental approved IdP’s, trusted partner IdP’s or publicly available user stores like Google, Apple or Facebook. One can decide which privilege's to assign for various user stores dependent on credibility and the latter examples are often given lower access or authorization levels to digital assets given its public nature.
- Step 4 – Zero Trust: Zero Trust starts by assuming that any identity – whether human or machine – with access to your applications and systems may have been compromised. The “assume breach” mentality requires vigilance and thus a Zero Trust approach to security. With a Zero Trust approach to identification and authentication, you can let users use various IdP’s, but trust is very limited in time and the identity is always challenged. For your users this approach can both make it easier to work with digital innovation and transformation, as business development is not restricted by identity and security management, but it also requires a very aware strategy for identity management and high level of maturity as to IAM and secrets management, which can be awkward for your users.
When you know the maturity of your IAM; it is time to think about which aspects of IAM (and its sibling consumer/customer IAM - CIAM), that are applicable and important to you and your organisation!



