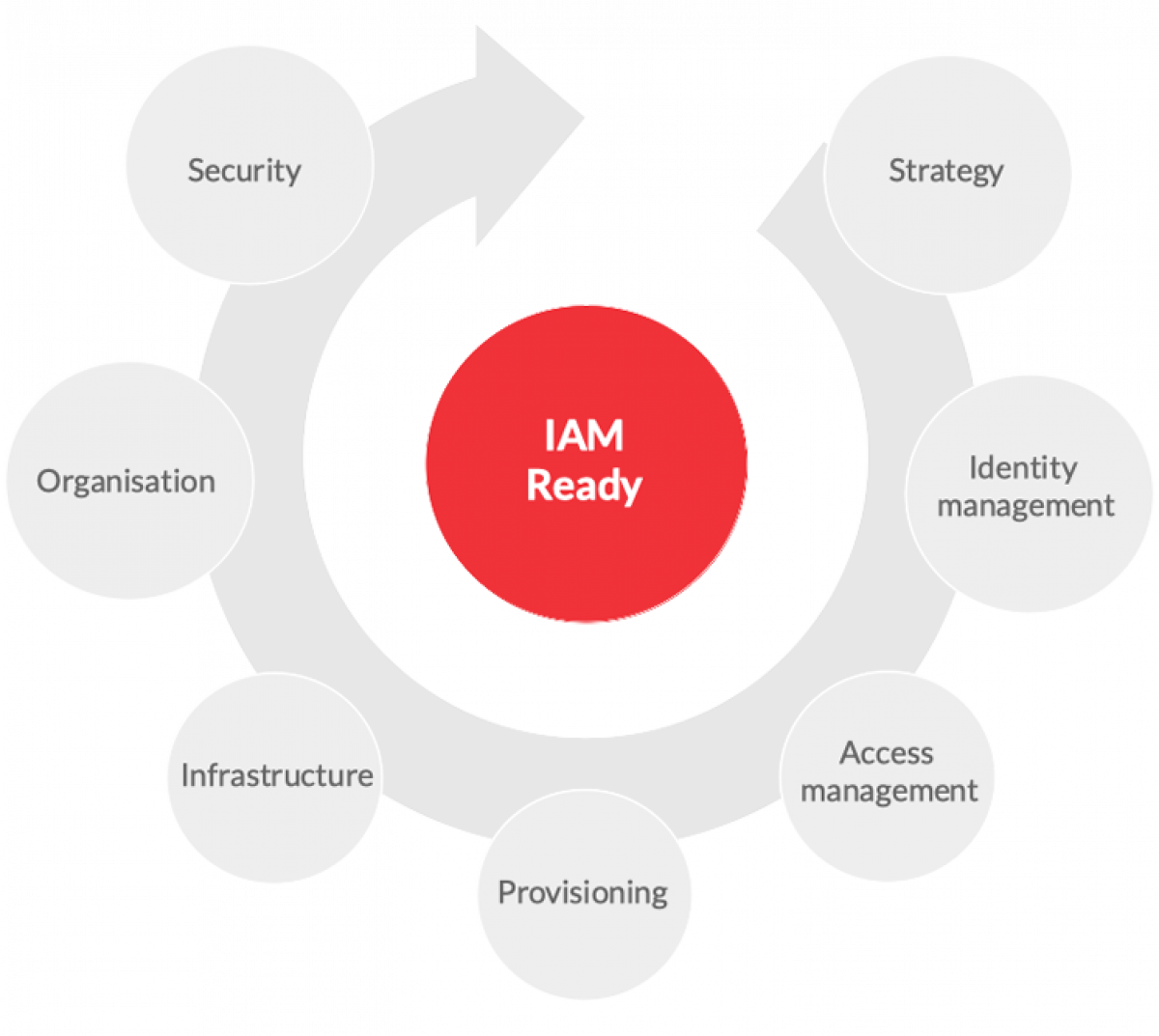
The figure above represents the Redpill Linpro IAM Ready model we use when assisting customers with IAM needs. It represents our hard earned real life experiences and by using it we verify that important aspects aren't ignored or forgotten.
The figure shows the steps for finding your IAM solutions and what aspects you need to consider to make sure you fulfill your IAM needs. Each section of the model is outlined below:
Strategy
As proven many times before; Without a clear strategy, you will make more mistakes, often miss your target and you will be unable to make nessessary decisions. Some key components of your IAM strategy should be:
- Identity, user groups (external/internal) and user group segmentation
- Authentication, authorization, federation and access control
- Structure, integrations, asset protection and credential management
- Identity lifecycle management
- Risks, security awareness monitoring and oversight
- Liabilities, compliance, governance and SLAs
- Ethics, employee training, organization
- And finally; Platform, systems, cloud/on-prem/SaaS for your IAM solutions
As you can see; the strategy provide the overview and represents the guiding principles for the other areas (like identity management and security), but will also provide many important guidelines going forward. The strategy will keep the rest of your assessment together, set the tone and be the "red line" or compass when making descisions and taking action for your IAM solutions.
To be successful with your IAM initiative, you will also need to make sure that the strategy is anchored with and supported by your executive management. Without proper backing by management, it will be hard to implement decisions and get organisational support for your initiative. Remember that implementing new principles for identity management often also requires buy in from the organisation.
With a clear and undisputed sponsorship from the adequate management level makes this process a lot easier.
Identity management
Identity Management (IDM) is a fundamental component of your IAM project. IDM refers to the processes, methods and tools used to manage digital identities for individuals, entities, and devices within your digital ecosystem. The primary goal of IDM is to ensure that the right individuals (entity), have appropriate access.
This step of your IAM Ready initiative is also about SSO, MFA, federation, governance, content, biometrics, secrets, credentials and (dont forget) identity lifecycle management.
Access management
While Identity Management (IDM), focuse on managing digital identities and their attributes, Access Management is about controlling and regulating the access that these identities have to resources within your IT and digital environment.
It ensures that appropriate permissions are granted for access to specific resources, while enforcing security policies and compliance requirements. In this step of the assessment you will also establish what standardes to use, such as: Basic auth, mutual TLS, certificate usage, oauth2, SAML, open-id connect, Kerberos, etc.
Are you only using standards? Or are you relying on proprietary accesses from from the likes of external providers, such as BankId or AppleID.
Provisioning
Provisioning is the process of granting, managing, and revoking access rights and permissions to various resources (such as systems, applications, databases, and more), for users within an organization. It is a crucial component of IAM because it ensures that appropriate access is given to resources, while the security and compliance remains. Some key aspects of provisioning is
- User On-boarding/Off-boarding
- Access Management
- Automation of provisioning
- Compliance with regulatory requirements and internal security policies
Infrastructure
The IAM infrastructure are foundational components and technologies that you implement to manage and secure digital identities, as well as control access to resources and services.
Your IAM infrastructure serves as the backbone (carrying your IAM strategy), and should enable effective management of identities, access control, and security.
Your organization will most certainly already have IAM infrastructure – but does it carry your needs and align with your strategy?
Some key elements of your infrastructure will be:
- Directory services and identity stores
- Authentication and authorization services
- Techniques and automation of provisioning and identity lifecycle management
- Storage, cloud, servers and other integrated systems
- ... and much more
Depending on your home country, you may also have regulations and laws to take into account when looking at your infrastructure – for instance; Are you allowed to store user data in a Cloud or SaaS IAM solution?
Organization
The organization around your IAM is oftentimes forgotten (or at least neglected). Your IAM infrastructure and solutions will provide the ground on which to stand, but your organization need to be trained and be ready for the daily identity tasks. When organizing your business to be aligned with your IAM strategy we suggest you look at concepts such as roles, responsibilities, communication, support, crisis-management, admin delegation control/protocol, security and more.
You must also determine the organization for supporting the identity life cycle, IE. who is responsible for adding and removing an identity (HR for users and IT for services?), and also make sure that the ones responsible have the full picture of your IAM and any separate system with identities and accesses.
Security
The security of your company or government is probably already being tested. Either you are being probed by outside forces, or you are running your own penetration tests, white hack projects or GDPR/information security audits. Forgetting that your security situation starts with identities (IAM), is more common than we expect.
We focus on aligning your routines, rules/policies, organization, audit/logs/monitoring, incident management, admin delegation policies, identity auditing, as well as access control threats (password handling/cracking, privileges escalation, social engineering, IAM infra vulnerabilities).
Are you (IAM) Ready?
So finally! Do you have a strategy? Does it cover the aspects above? Are you sure and did you test it? We hope that the blogs provided so far will make you think about your identitites and accesses more as a key component (or even digital heart), or your entire system, rather than something each system owner will fix as a minor detail.
Digital identitites, like integration, is a central engine of your digitalization and since most companies already move focus from "IT as a must" to "IT as core business", we all need to care more about IAM to be prepared – to be IAM Ready!



