Given the focus on security breaches leaking account information the last few years, we have taken a fresh look at how secure our LDAP passwords really are, and if we can let OpenLDAP use a modern hash algorithm.
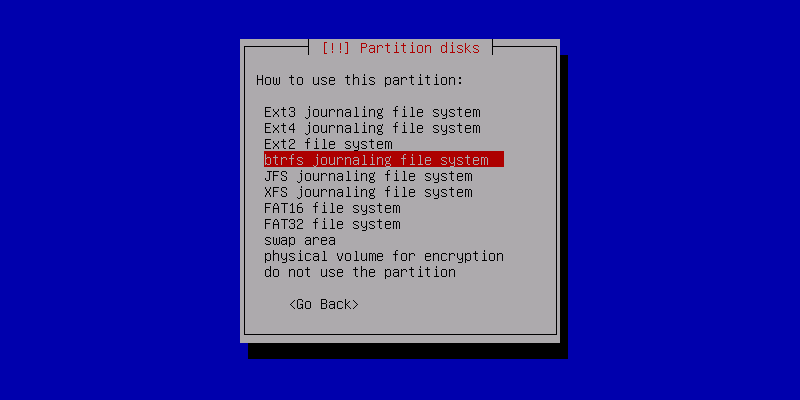
... [continue reading]Encrypted Btrfs for Lazy Road Warriors' laptops
Why Btrfs?
Btrfs is full of new features to take advantage of, such as copy-on-write, storage pools, checksums, support for 16 exabyte file-systems, online grow and shrink, and space-efficient live snapshots. So, if you are used to mange storage with LVM and RAID, Btrfs can replace ... [continue reading]
varnish-4.1.3 and varnish-modules-0.9.1 for fedora and EPEL
The Varnish Cache project recently released varnish-4.1.3 and varnish-modules-0.9.1. Of course, we want updated RPMs for Fedora and EPEL.
... [continue reading]Setting up Jekyll
So, management wants a microsite for blog-entries ASAP, while the techs wants to use tools they are used to - markdown and git. On top of that, we have a limited spare time for implementing a new solution.
In the intersection of that lies Jekyll!
... [continue reading]RedHat Performance Tuning
Performance tuning is done to increase system performance, reduce power usage or to ease the application impact on the rest of the system. If done prematurely, or without any measurements, performance tuning may, of course, have the opposite effect.
But done systematically, performance tuning can be more of a science than an art form.
The method
Start by figuring out what the “normal” situation is.
Look for potential performance issues, and adjust tuning parameters to fix them. Look for ... [continue reading]
Logging elapse time in Apache and Nginx
Logging the elapse time in the web server access log can be very useful for statistics and problem solving. I usually throw it in at the end of the log line (that’s generally compatible with existing log-analysis tools like awstats), and on a keyword=value format so that it’s easy to grep out. There is a small performance cost, though.
The elapse time includes everything - when filtering out log lines with high elapse-time you may typically find mobile clients downloadi ... [continue reading]
Quick Remote File Access
Sometimes it is be nice to mount a path from a remote file system as if it was local. Setting up NFS or Samba may be a lot of hassle, and may require root access on one or both of the boxes. Enter FUSE and SSHFS.
FUSE makes it possible to implement a file-system in a user-space program. Lots of such programs exists, making it possible to access web sites, blogs, your android, google drive, your google mail and lots ... [continue reading]
SSH autocompletion, jump host automation and other tips
OpenSSH is a flexible tool for not only logging into other servers, but to also help tunnel other network traffic. The following article is a grab-bag of useful SSH tips.
SSH per-user configuration file
Using the per-user configuration file, ~/.ssh/config you can make your life a bit easier. One common scenario is that a SSH server you commonly use is listening on a non-standard port. To save you from the strain of typing out -p ... [continue reading]
Recording and replaying console sessions
Ever wanted to record a log of an interactive console session? Easy, just use the script utility. It’s probably already present on your system, no installation required.
To start recording, run script --timing=script.tim script.log. This spawns a new shell, recording stops when you exit from it.
To replay the log, run scriptreplay script.tim script.log. It is also possible to speed up or slow down the playback speed. For example, in order to play back ... [continue reading]
Oh, Molly!
I’m sure we all have had “that feeling once”. You patch your desktop or laptop, then type in reboot in a shell in order to boot your computer. And that crucial server you were working on starts shutting down.
But fear not - a solution exists for this and similar problems.
History
Molly-guard was (according to Internet) originally a improvised plexiglass cover shielding the kill switch on an IBM 4341. It was named after a programmers daughter - Molly ... [continue reading]